From Squirrelly Dreams to Digital Streams: Our Blog Debuts
Discover the inspiration behind The Programming Squirrel, explore our tech-savvy content lineup, and join our vibrant community of cybersecurity enthusiasts and curious minds.
Table of Contents 🪑
- 🎯 Objectives
- Who is this blog for? 🐿️
- Why a Cybersecurity Blog? 🛡️
- Who We Are and What We Offer 👩🏼💻
- What to Expect from The Programming Squirrel 📥
- Advocacy for Women in Cybersecurity and Technology 👩🏼💻
- Our Vision for the Future 🔮
- How You Can Get Involved Today? 🗳️
- Key Takeaways ✌🏻
- Footnotes 🔗

🎯 Objectives
Inform Readers
- Introduce The Programming Squirrel as a fresh and exciting cybersecurity blog.
- Highlight the blog’s purpose: to provide engaging, accessible, and expert-driven content about cybersecurity, tech certifications, and digital security trends.
- Showcase the playful yet professional tone that sets the blog apart from others.
Create Emotional Engagement
- Make readers feel welcomed into a vibrant and inclusive community of tech enthusiasts.
- Spark excitement and curiosity about the blog’s offerings, with a mix of fun branding (the “squirrelly dreams”) and serious value (the “digital streams”).
- Build trust and credibility by emphasizing the team’s expertise and commitment to quality content.
Drive Action
- Encourage readers to subscribe to the blog’s newsletter for regular updates.
- Prompt them to explore the website including the first few blog posts or resource sections.
- Inspire them to share the debut post with their network, spreading the word about The Programming Squirrel.
Who is this blog for? 🐿️
This blog targets a tech-savvy, forward-thinking audience interested in cybersecurity, technology trends, and digital innovation. It’s particularly appealing to:
- Cybersecurity Enthusiasts: Professionals, hobbyists, and students looking to stay informed about the latest trends, tools, and best practices in cybersecurity.
- Tech Blog Explorers: Readers who enjoy discovering fresh unique voices in the tech blogging world, especially with a playful and engaging tone.
- Digital Learners: Individuals seeking accessible and actionable content to improve their cybersecurity knowledge or earn certifications.
- Industry Insiders: Tech professionals, content creators, and influencers interested in building connections or partnerships with new blogs.
Why a Cybersecurity Blog? 🛡️
Cybersecurity is quickly taking over our lives. From the rising sophistication of foreign and domestic cybercrimes Cybercrimes are illegal activities that involve the use of computers, networks, or digital devices to commit crimes. These offenses are typically perpetrated online or through digital means, and they can target individuals, organizations, or governments. Cybercrimes range from non-violent crimes such as data theft to more serious offenses like hacking or cyber terrorism. to government deployment of AI to protect our sensitive data; the world is a very different place now. Below is an infographic put out by NIST National Institute of Standards and Technology. 1 highlighting the integral role these technologies are playing in this spy v. spy tug of war.
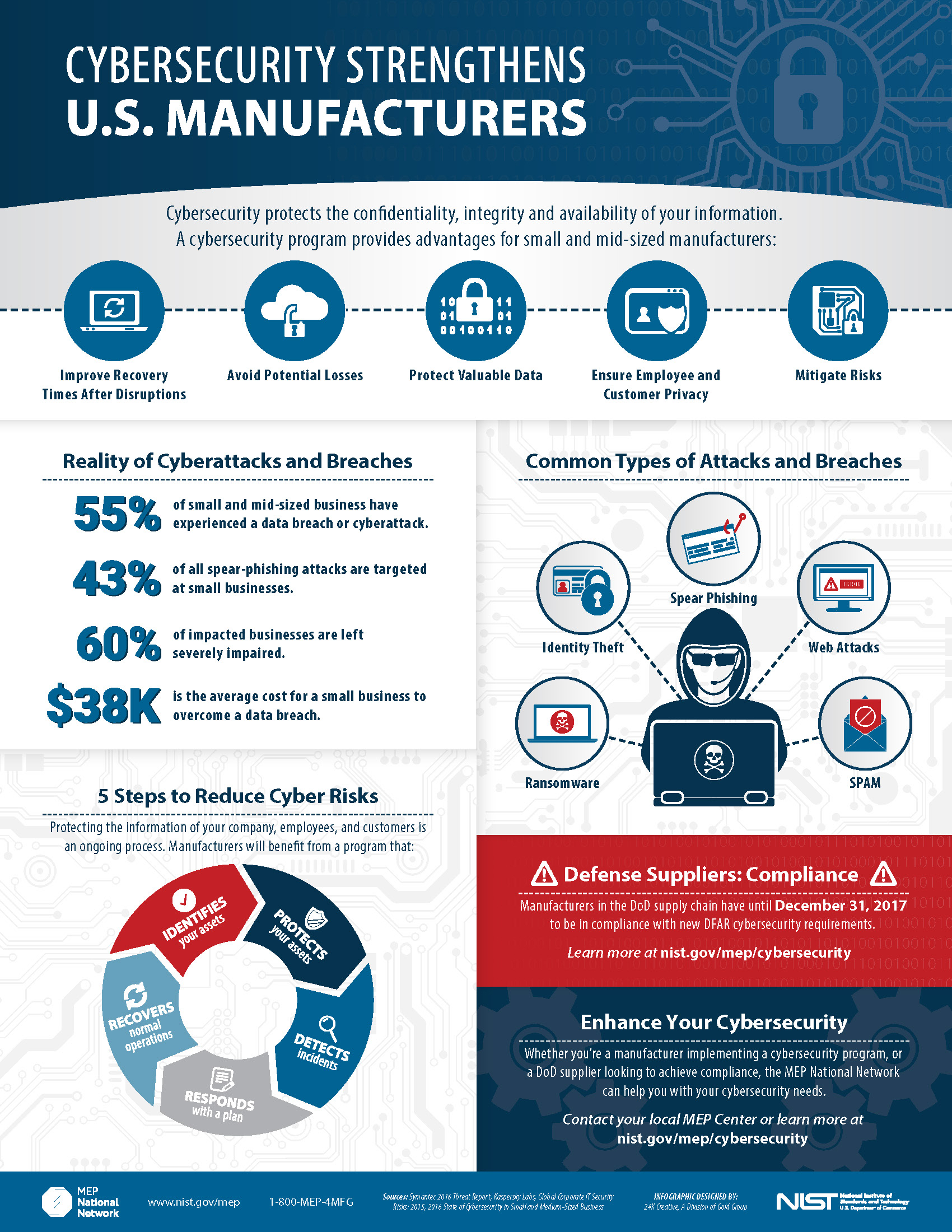
AI is playing a huge role in this cascading effect. Hackers can employ natural language models to trick victims into giving up valuable information or use data mining to gather vast amounts of PII In the context of cybersecurity, PII refers to any data that can be used to identify an individual, either directly or when combined with other information. Protecting PII is crucial to safeguarding privacy and preventing identity theft, fraud, or unauthorized access. for use in phishing or ransomware attacks. Meanwhile, world governments utilize AI to leverage encryption algorithms as well as gather intelligence and incite cyber warfare. This is the battlefield of today, fought not on land or water but on bytes.
If you look carefully at figure 2, there are plenty of measures one can take to stay on top of their privacy, but will it ever be enough? It seems like even as the good guys get good, the bad guys get worse… In walk, bigger good guys. And then even worse bad guys. And on and on the wheel goes. But this feedback loop is perhaps the greatest reason that we need to invest our time and energy into the subject because it’s either we do it or they do.
Why Does the World Need Another Cybersecurity Blog?
One of the major pain points I hear on the subject of cybersecurity is that its jargon and rapid pace make it difficult to tread water. That there aren’t enough hours in the day to read every CVE In cybersecurity, CVE is a publicly disclosed database that tracks known security vulnerabilities and exposures in software, hardware, and firmware. Each CVE entry is assigned a unique identifier to help security professionals and organizations quickly reference and address these issues. or zero-day A zero-day is a security flaw or weakness in software, hardware, or firmware that is unknown to the vendor or developer, making it vulnerable to exploitation by attackers before a fix or patch is released. The term “zero-day” refers to the fact that the vendor has “zero days” to fix the vulnerability because they are unaware of it, and thus there is no protection available when the vulnerability is first discovered. report. And to some extent, this is pretty true. I mean, cyber moves fast! The vulnerability remediation timeline (the time from detection to patch release) on the most critical CVEs is usually between 5 and 14 days but can run up to 39 days if the bug is less severe2. These findings were corroborated by Google’s Threat Intelligence team who found that hackers only have between 1 and 4 days to exploit before a patch is released, a number that’s going down overall3.
🖊️ Note
Links to both of these peer-reviewed reports can be found at the bottom of the article in the Footnotes 🔗 section. You may also follow the footnote quick reference links.
Protecting clients’ data, especially in response to a breach is of the utmost importance. Quick recovery is key to not only saving your reputation in the tech industry but also your bottom line. Adding to the drama of the business, Government sanctions, and incentives have become a common way to combat flagrant negligence security compliance as lawmakers struggle to keep data leaks from destabilizing the industry. In healthcare for instance, HIPAA HIPAA is a U.S. law designed to protect the privacy and security of individuals’ health information. From a cybersecurity standpoint, HIPAA establishes standards and regulations that health-related organizations must follow to safeguard Protected Health Information (PHI) from unauthorized access, breaches, and misuse. standards and benchmarks put a price on protecting patients’ health-related PPI to the tune of millions of USD for mishandling a single case. Cyber jobs are risky business! If you think like me, that’s also what makes cybersecurity so enticing for insiders who get it.
Perhaps the biggest detractor from jumping headlong into a cyber career is the lack of any practical way to gain a foothold in the industry. The roadmap to becoming a, say a cybersecurity analyst Responsible for protecting an organization’s systems, networks, and data from cyber threats. They monitor for suspicious activity, analyze security risks, and implement measures to prevent, detect, and respond to cyber attacks. Cybersecurity Analysts often work as part of a larger security team, supporting the organization’s overall cybersecurity strategy. , or penetration tester A cybersecurity professional responsible for simulating cyber attacks to identify vulnerabilities in an organization’s systems, networks, and applications. Pen Testers use ethical hacking techniques to assess security controls and provide actionable recommendations to improve defenses. is not only expensive, requiring both a college degree and ongoing certifications, but it’s also contradictory at times. First, you need this many years of experience, then you need these certifications, but to get these certifications you need this experience and these networking connections. I have boiled down a little of what these qualifications are to give you an idea, but this is by no means the best or only path; heck, it’s probably not even the exact one we will follow throughout our cyber education at The Programming Squirrel. It’s just a hyper-high-level analysis of top careers in the industry and how to qualify for them.
Qualifications for Various Cyber Job Titles and Respective Pay Benefit Summary:
- Years of Experience: Entry-level jobs (0-2 years); Mid-level (2-5 years); Senior-level (5-10 years).
- Education: A bachelor’s degree is the minimum requirement, with master’s degrees preferred for executive roles.
- Certifications: Security+, CEH, CISSP, CISM, OSCP, and others enhance job prospects.
- Most Important Factors: Certifications, hands-on experience, and continuous learning are key.
- Salary Impact: Meeting these requirements (with certifications and experience) can increase base salaries by $10,000 to $40,000+ annually, with top executives like CISOs earning significantly more.
🔗 Resources
The above analysis and summary are based on these sources but there is enough material here for another blog article or five! So I will leave these here until I have a chance to thoroughly go through them.
- Coursera. (2025, January 15). Your Cybersecurity salary guide. https://www.coursera.org/articles/cybersecurity-salary?
- Cyber Security salary (Senior, Mid & Entry-Level Pay 2025). (2025, January 2).
- Cyber Security Education. https://www.cybersecurityeducation.org/degree/salary/?
- Fox News. (2025, January 8). Outgoing WH official calls for US to bolster cybersecurity workforce by hiring non-degree holders. New York Post. https://nypost.com/2025/01/08/us-news/outgoing-wh-cyber-director-harry-coker-calls-for-us-to-bolster-cybersecurity-workforce-by-hiring-non-degree-holders/?
- Indeed Editorial Team. (2023, October 2). Guide to Entry-Level Cybersecurity Job Requirements. Indeed Career Guide. https://www.indeed.com/career-advice/finding-a-job/entry-level-cyber-security-jobs-requirements
- Information Security Analysts. (2024, August 29). Bureau of Labor Statistics. https://www.bls.gov/ooh/computer-and-information-technology/information-security-analysts.htm?
- Moore, M., PhD. (2025, January 14). How to become a cybersecurity specialist [+ Career & Salary guide]. University of San Diego Online Degrees. https://onlinedegrees.sandiego.edu/cyber-security-specialist-career-guide/
- Stupp, C. (2024, October 2). Pay rises for cyber chiefs as hacks and regulatory pressure increase. WSJ. https://www.wsj.com/articles/pay-rises-for-cyber-chiefs-as-hacks-regulatory-pressure-increase-1bf737d9?
- Witcher, R. (2024, September 26). 10 Highest-Paid Cybersecurity jobs and their salaries. Destination Certification. https://destcert.com/resources/highest-paid-cybersecurity-jobs/?
Cyber employers want someone who has a degree but who invests their time into keeping up with the hottest trends, languages, OpSec A systematic process used to identify and protect sensitive information from being accessed or exploited by adversaries. Originally developed by the U.S. military, OPSEC is now widely used across various industries to safeguard critical information and minimize vulnerabilities. standards, and techniques. They want a near-constant commitment to education and honing your skills. Mid-level roles also require 2-5 years of experience which can be tricky if you’re just coming out of college, especially in this saturated market. Certification exams are one of the best ways to set yourself apart from everyone in your graduating class. Entry-level certs that you should get immediately are:
- CompTIA Security+: Widely recognized for foundational security knowledge.
- Certified Ethical Hacker (CEH): Excellent for those focused on penetration testing and ethical hacking.
- Certified Information Systems Security Professional (CISSP): Ideal for those aiming for managerial or higher-level roles.
- Certified Information Security Manager (CISM): Helps for those pursuing leadership roles in cybersecurity.
- Cisco Certified CyberOps Associate: Good for those focusing on network security operations.
While those are great starting points, specialized roles like Information Security Manager The Information Security Manager ensures effective implementation of security policies, proactive risk identification and mitigation, prompt response to incidents to minimize impact, and continuous alignment of security efforts with business goals. and CISO The CISO ensures that data integrity and confidentiality are maintained, reputation risks are minimized by preventing breaches, regulatory penalties are avoided through compliance, and the organization is prepared to face evolving cyber threats. that boast a $565,000 salary want you to have the following advanced certifications:
- Offensive Security Certified Professional (OSCP): Highly respected in the penetration testing and ethical hacking community.
- Certified Cloud Security Professional (CCSP): Key for those entering cloud security.
- Certified Chief Information Security Officer (CCISO): Best for individuals targeting executive roles like CISO.
- GIAC Security Essentials (GSEC): Ideal for professionals who need to demonstrate their practical security skills.
The bottom line? You want to be in cyber, trust me, but it’s going to be tough getting there. That’s where we come in with the big guns. Study guides, cheat sheets, labs, synthesis and notes for certification exam studies, and a one-of-a-kind open and inclusive community are all waiting for you here at The Programming Squirrel. This blog and our host of resources in various mediums and platforms simplify cybersecurity topics and present them in a playful, relatable tone that can appeal to everyone, from novices to seasoned professionals.

How Does The Programming Squirrel Stand Out?
As the sheer volume of cyber threats grows daily, the job market for good, qualified cyber professionals grows in tandem. Helping you cut through the massive amounts of inaccessible and overly technical resources online is The Programming Squirrel. Having all your cyber news, resume building, certification study materials, expert insights, mentorship, and collaborative networking event opportunities in one place can give you the leg up that you need to break into this highly selective field. And, unlike other blogs, we blend expert insights with a light-hearted, engaging approach that makes cybersecurity both informative and enjoyable.
Who We Are and What We Offer 👩🏼💻
The Programming Squirrel was founded by cybersecurity enthusiast Nyki Anderson, who like you, is on that dream job journey. Her passion, homegrown expertise, and commitment to bringing cyber to under-represented groups (especially women) necessitated her start The Programming Squirrel for all those who need it. Her love of sharing through writing blogs, developing tutorials, video walkthroughs and labs, certification guides, industry updates, and community discussion is what makes us special. With much of this content completely free to boot, there’s no end to what is possible if you stick with us!
Plus, we do it in style. A unique blend of playful yet professional and our brand’s dedication to building a community of learners and professionals, The Programming Squirrel has that winning mix. You are inundated by heavy, overly technical blogs, isn’t it time you opted for a youthful and fresh take on the subject?

Who’s Behind The Programming Squirrel
Currently, our small team consists mainly of Nyki and a few helping minds who advise her but who wish to remain anonymous. As a brand in its infancy, Nyki wears many hats. To her credit, the orchestration of complex, multilayered projects is part of what gives her an edge in the industry. Originally majoring in mathematics, she took her first computer science course in freshman year as a general education requirement; the rest is history. From that first class (Intro to Python and Java) to today, she has never stopped picking up new languages and skills; often starting and then restarting projects as she goes down the “coding rabbit hole”. Her appetite for all things programming is voracious and borderline obsessive. But her love of the struggle fuels the intensity necessary to run The Programming Squirrel.
What started as tutoring in math for work-study soon became a private venture where she would host study events on Discord for classmates. With her phone on an extendible arm above the desk, she would walk her peers through problems, carefully explaining the do’s, don’ts, and “gotchas” of the concepts. Before to this, she had enjoyed documenting her personal coding projects and translating them into detailed tutorials that she’d post to her GitHub and StackOverflow hoping they’d save some coder, somewhere in need. These endeavors became such a joy for Nyki, that she knew she had to streamline the knowledge-sharing process and devote time to this growing passion. The brainchild of this coming-of-age story is The Programming Squirrel, a space for exploration, deep understanding, networking, and certification exam-kicking awesomeness. A place to strengthen your skills regularly so you can land the job of your dreams and have a little fun along the way!
In cyber, it’s all about accessibility and often, who you know. So the community aspects cannot be overlooked here. With a budding following on Discord and a social media presence on several popular platforms, there’s a space for everybody at this table. Hosting discussions, special live events, challenges and labs, study groups, and so much more, The Programming Squirrel and its brand are both a trusted source for cyber resources and a candid forum for authentic discourse. Join us as we break down barriers, empower ourselves and others to succeed in the cyber industry, and overall #win at life!

What to Expect from The Programming Squirrel 📥
So what types of content will The Programming Squirrel cover? In the beginning, at least, much of the content will focus on passing those certification exams. Starting of course with the CompTIA Security+ certification exam. To keep things as interactive as possible, we will most likely be jumping back and forth between that and the Burp Suite Certified Practitioner labs at Portswigger Academy. Both of these certs are a feather in any young cyber analyst’s cap. Regularly we will feature certification refresher courses as well as news updates via our digital newsletter regarding changes to exam curricula or concepts. The cyber world is constantly evolving, and staying up-to-date with the latest ethical hacking techniques and breaking bugs will be paramount to staying at the top of your field.
You can also expect tutorials and lab walkthroughs for popular online hacking courses including HackTheBox, Portswigger Academy, and more. Often, these will take the form of a blog article but we will experiment with video formats and platforms such as YouTube and Vimeo. Taking the time to go through these walkthroughs will play a big role in developing your knowledge base and challenging you to solve puzzles on a regular basis. This will be the bread and butter of our brand.
Finally, community platforms such as Discord and social media posts will round out content offerings by providing a space to converse with other cyber hopefuls and professionals. Diversity and inclusion are values at the very heart of The Programming Squirrel’s inception. Cultivating a community of positivity and growth cannot be done alone and requires every one of you to be successful. Respond to posts and answer questions if you are knowledgeable. Don’t be afraid to put yourself out there because you never know who can be a friend or resource in the future. We will try our best to be active and personally available to answer any questions or listen to your valuable feedback. DM us on any of our socials and we will take care to respond within 1-2 days usually.
How Often Will the Blog Be Updated?
Content schedules will be posted across our socials in the Monthly Social Media Schedule. At least in the beginning, these schedules will be tentative as we integrate The Programming Squirrel into our busy lives but we will do our best to keep regular updates and new content rolling out. Subscribing to The Programming Squirrel Newsletter will be your most direct line to what’s going on, not only within our community but the greater cyber world. Keep an eye on your inbox for announcements and edits to the schedule.
Support & Premium Content
Providing free online resources is important to growing our value as a brand. While we offer several tiers of premium content on our Patreon, you can still expect valuable resources without a subscription. However, supporters and insiders will gain access to premium Discord channels, have early access and sneak peeks at upcoming content, receive downloadable formats of popular guides and courses, as well as be invited to exclusive webinars and events throughout the year. Your vote of confidence and financial backing will help The Programming Squirrel grow and help us continue to provide powerful content and enrich our community.
You can also support us on GitHub Sponsors. For all those eager to join our insider’s programs, we wholeheartedly thank you and will work diligently to make your investment worthwhile.
Advocacy for Women in Cybersecurity and Technology 👩🏼💻
Besides providing high-quality cybersecurity resources, The Programming Squirrel is an active advocate for women in the cyber industry. We are members of several organizations dedicated to breaking down barriers for women and underrepresented groups pursuing cybersecurity careers. Join us by following and supporting these women-centric organizations:
- Women in Security and Privacy (WISP)
- We Are Tech Women
- Hackers In Heels
- Women in Cyber Security (WiCyS)
- Girls Can Hack
- Women Cybersecurity Society
For events and other ways to show your support, subscribe to our newsletter.
Our Vision for the Future 🔮
At The Programming Squirrel, we envision a world where cybersecurity is not just a profession but a community powered by diversity, accessibility, and innovation. We’re committed to breaking barriers and ensuring that underrepresented voices, especially women, find their place and thrive in this dynamic industry.
Our vision is fueled by three guiding principles:
- Empowerment through Knowledge: We believe knowledge is the ultimate equalizer. By creating hands-on resources, interactive tutorials, and real-world challenges, we empower learners to build confidence, master technical skills, and navigate the complexities of cybersecurity with ease.
- Accessibility for All: Cybersecurity should be for everyone. We’re dedicated to making learning approachable and inclusive by demystifying technical jargon and designing content that resonates with both beginners and seasoned professionals.
- Community-Driven Growth: Learning is a lifelong adventure best enjoyed together. That’s why we’re cultivating a supportive community where aspiring professionals can connect, collaborate, and celebrate their wins. Together, we can inspire one another to achieve more.
What’s Next for The Programming Squirrel?
As we look to the future, we aim to expand our reach through:
- Video tutorials and full-length interactive courses;
- Partnerships with industry leaders and other organizations with similar goals;
- Offer mentorship and internship programs; and
- Host cybersecurity conferences and webinars.
In these ways, we will reinforce our mission to be a trusted resource and catalyst for growth in the cybersecurity space as well as create opportunities that open doors for the next generation of cybersecurity professionals. Eventually, this will mean registering The Programming Squirrel as an LLC.
How Can You Shape the Future of The Programming Squirrel?
Followers and fans of the brand can have a real influence on its direction by sharing feedback, suggesting topics, and actively engaging in the community. There are several forums for doing so including directly emailing us at nyki@the-programming-squirrel.com or sliding in our DMs on any of our social media platforms.
How You Can Get Involved Today? 🗳️

Ready to dive into a world where cybersecurity meets creativity? Join the Squirrel Squad today!
- Subscribe to our newsletter to unlock exclusive tips, tutorials, and insider updates.
- Follow us on social media to connect with a community of like-minded tech enthusiasts.
- Share this debut post with your network to spread the word about our mission to make cybersecurity accessible and fun!
Don’t wait — take your first step into our squirrelly world of digital security and inspiration now!
Key Takeaways ✌🏻
-
🛡️ Complexity of Cybersecurity: The fast-paced nature of cybersecurity makes it difficult for individuals to stay informed about the latest threats and best practices. The blog aims to simplify these topics and make them accessible to a broader audience. Cybersecurity professionals often face challenges in keeping up with rapidly changing vulnerabilities, emphasizing the need for reliable and digestible information.
-
🧠 Need for Community: The Programming Squirrel recognizes that learning is best done in a supportive community. By fostering a collaborative environment, the blog aims to empower individuals to share knowledge, experiences, and resources, making cybersecurity a more approachable field for everyone.
-
📈 Career Pathway Insights: The blog provides a roadmap for budding cybersecurity professionals, detailing the qualifications and experiences needed to succeed in the industry. This insight is crucial as many individuals may feel overwhelmed by the barriers to entry, which often include extensive education and certifications.
-
🤖 Role of AI in Cybersecurity: The increasing sophistication of cyber threats, particularly those utilizing AI, highlights the importance of understanding both the offensive and defensive aspects of cybersecurity. The blog discusses how AI is both a tool for hackers and a means of defense, illustrating the dual-edged nature of technology in this field.
-
🌟 Certification Emphasis: The focus on certifications such as CompTIA Security+ and CEH is essential for career advancement in cybersecurity. The blog aims to provide resources and guidance to help individuals prepare for these important exams, which can significantly enhance job prospects and salaries.
-
💬 Engaging Tone: The blend of playful yet professional communication sets The Programming Squirrel apart from traditional, more technical cybersecurity blogs. This approach not only makes content more engaging but also helps demystify complex topics, making them easier to understand.
-
👩💻 Advocacy for Diversity: The blog’s commitment to advocating for women and underrepresented groups in technology is a critical aspect of its mission. This focus not only enriches the community but also aligns with the broader industry trends towards diversity and inclusion, fostering a more equitable landscape in cybersecurity.
The Programming Squirrel is set to transform how individuals approach learning in the cybersecurity space, making it more engaging, accessible, and community-oriented. With a proactive approach to tackling the industry’s complexities and a strong emphasis on inclusivity, it promises to be a valuable resource for anyone looking to navigate the ever-evolving world of digital security.
Footnotes 🔗
-
Cybersecurity strengthens U.S. manufacturers. (2024, July 17). NIST. https://www.nist.gov/mep/manufacturing-infographics/cybersecurity-strengthens-us-manufacturers ↩
-
Sivadasan, A. (2024, November 30). Vulnerability Remediation: how fast should you patch? https://allaboutgrc.com/vulnerability-remediation-timelines-how-fast-should-you-patch/? ↩
-
Mandiant. (2024, October 15). How low can you go? An Analysis of 2023 Time-to-Exploit Trends. Google Cloud Blog. https://cloud.google.com/blog/topics/threat-intelligence/time-to-exploit-trends-2023? ↩